You wouldn’t have your hospital doors left wide open at night, so why are thousands of your connected healthcare devices still left at risk to known vulnerabilities? Hospitals and health systems are more technologically advanced in 2025 than ever before. But so is that innovation a quiet, constant threat: unsecured (Internet of Medical Things) IoMT devices.
From ventilators to surgical robots, these devices are critical to the delivery of care, yet many are operating on out-of-date firmware, defaulting to default usernames and passwords, or openly exposed to the internet. It’s a blind spot when it comes to security that’s too important to overlook.
Protecting IoMT devices is mission-critical for healthcare in 2025. It’s no longer IT’s or the CISO’s to-do item; it’s a boardroom imperative, a clinical necessity, and a reputational protection. The stakes are greater than ever, and the risks of not acting are no longer hypothetical.
In this article, we’ll explore why healthcare must act now, how the most exposed devices are putting patients at risk, and which proven strategies health leaders are using to protect their networks, without compromising care.
The Growing Risk: When Connectivity Outpaces Security
In healthcare’s digital evolution, every connected device is a double-edged sword. While IoMT devices have unlocked smarter diagnostics, faster care, and real-time patient monitoring, they’ve also introduced a new and often underestimated layer of exposure. The truth is that connectivity is accelerating faster than most organizations can secure it.
The Numbers Paint a Stark Picture
As per Claroty’s 2025 State of Cyber-Physical Systems Security report, 99% of healthcare systems contain medical devices with known exploited vulnerabilities (KEVs). Alarmingly, 89% of them are internet-directly connected and thus easily detectable by attackers.
These are not unusual edge cases. Devices such as MRI scanners, infusion pumps, and ventilators, central to hospital functioning, are precisely the ones most vulnerable.
From Vulnerability to Impact
When an IoMT device is hacked, the harm doesn’t stop at stolen information. Consider: delayed procedures, diverted emergency services, or surgeries halted in progress. Healthcare breaches alone in 2024 affected more than 276 million people, a daily average of 758,000 patients.
It’s not about fear-mongering. It’s about acknowledging that securing IoMT devices is mission-critical for healthcare in 2025 because it’s about lives, not systems.
What’s Making IoMT So Vulnerable?
If we know the risks, why hasn’t healthcare caught up? The answer lies in a complex mix of aging infrastructure, limited visibility, and security often treated as an afterthought during procurement. Let’s break down the key vulnerabilities putting today’s IoMT landscape at risk.
Legacy Devices Still in Use
Most of the hospitals have tight budgets and long procurement cycles. That usually translates to running devices that are 10-15 years old, with legacy operating systems that are no longer supported, no patches, no encryption, and limited access controls.
Default Settings and Insecure Protocols
A surprising number of devices still ship with hardcoded credentials. Even more troubling: many hospitals haven’t changed these defaults. When you add outdated protocols such as Telnet or FTP into the mix, it creates a clear opportunity for exploitation.
Increasing Sophistication of Threat Actors
In 2025, threat actors no longer have to brute-force their way into hospital networks. Numerous actors depend upon known vulnerabilities in exposed IoMT devices as footholds upon which to launch lateral movement across systems. Ransom gangs, specifically, prefer medical environments due to their immediacy and willingness to pay.
When an Ultrasound Machine Became a Trojan Horse
A regional U.S. hospital recently discovered its ultrasound system was communicating with an external server in Eastern Europe. The machine, installed in 2016, had never been updated. Threat actors had exploited a known vulnerability and used the device to quietly exfiltrate sensitive patient data over several months.
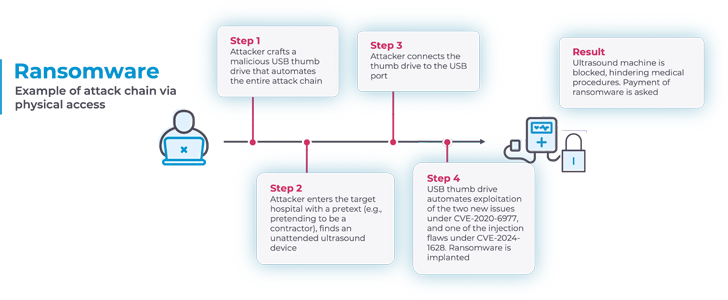
According to a technical report by operational technology (OT) security vendor Nozomi Networks, the consequences made possible by these vulnerabilities are diverse: they range from the installation of ransomware on the ultrasound machine to accessing and altering patient data kept on the susceptible devices.
No alarms were triggered. No symptoms appeared until a patient’s identity was compromised and flagged by a third-party credit bureau. The cost? A complete forensics sweep, brand damage, and HIPAA audit.
Why 2025 Demands a Rethink of IoMT Security
The Internet of Medical Things (IoMT) has transformed patient care, but it’s also opened a floodgate of new vulnerabilities. With billions of connected devices transmitting sensitive health data, healthcare organizations are no longer just care providers; they’re digital infrastructure operators.
In 2025, the traditional “check-the-box” approach to cybersecurity just won’t cut it. As attacks grow more sophisticated and regulators scramble to keep pace, leaders must shift their mindset: from one-time compliance to continuous, proactive security. Here’s why the old rules no longer apply, and what must change.
Compliance Alone Isn’t Enough
HIPAA, HITECH, and the new Cybersecurity Performance Goals from HHS are raising the bar, but they often lag behind emerging threats. Security must move from checklists to continuous action.
Healthcare Is the New Critical Infrastructure
In January 2025, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) formally elevated healthcare’s classification within national critical infrastructure, citing the systemic risks posed by unsecured medical technology.
Insurance Premiums Are on the Rise
Cyber insurers are tightening underwriting standards. Health systems whose practices do not show mature IoMT security practices have higher premiums, or worse, no coverage at all.
Top Strategies to Secure IoMT in 2025
Let’s explore the tactics that will make the biggest difference this year, starting with the riskiest endpoints.
1. Risk-Based Asset Prioritization
Begin by prioritizing the riskiest 5% of your device inventory. In Forescout and Claroty’s opinion, devices that are internet-facing and possess KEVs should be at the top of the list. They’re low-hanging fruit for an attack and high-impact for remediation.
2. Zero Trust for IoMT
Zero Trust is the new default architecture for secure healthcare IT. In the context of IoMT, that translates to authenticating all devices, every time, before permitting communication. Dynamic microsegmentation and contextual authentication are key enablers.
3. Real-Time Monitoring with AI
AI-driven platforms can monitor device behavior in real time, learning “normal” patterns and flagging anomalies immediately. This is particularly beneficial for IoMT, where conventional antivirus solutions do not work or are not present.
4. Secure Procurement and Vendor Accountability
Contracts for new devices should incorporate cybersecurity clauses that require security patch timelines, third-party risk assessments, and transparency regarding software bills of materials (SBOMs).
5. Continuous Staff Training
IoMT security is not a technology team effort alone. Nurses, radiologists, and biomedical engineers all engage with these devices daily. Secure practices, such as identifying phishing or reporting unusual device behavior, are ensured through yearly refresher training.
Future-Proofing IoMT Security
Securing today’s devices is essential, but staying ahead means thinking beyond today. As IoMT ecosystems grow more complex, healthcare leaders must look toward scalable, standards-driven solutions that can adapt to tomorrow’s challenges. Here’s what that future-ready mindset looks like in action.
Interoperability Will Require Stronger Standards
As healthcare systems incorporate more IoMT devices, ranging from remote patient monitors to smart beds, standardization will be paramount. The FDA, IEEE, and HIMSS are all converging on frameworks that require secure communication protocols among manufacturers.
Decentralized Device Identity
Studies by schools like Carnegie Mellon and Stanford indicate that blockchain and decentralized identity solutions would allow for secure, tamper-evident device authentication in real time.
Federated Threat Intelligence Sharing
Platforms such as Health-ISAC are making it possible to share real-time intelligence among hospitals, assisting entities in remaining ahead of active exploits that affect particular device types or manufacturers.
From Passive Risk to Proactive Resilience
Securing IoMT devices is now mission-critical for healthcare in 2025, not just as a technical necessity, but as a leadership imperative. Every infusion pump, MRI scanner, or connected ventilator is a vital link in the chain of patient care. But when those links are left exposed, the entire system becomes fragile. It’s no longer enough to react. The future belongs to healthcare systems that anticipate, fortify, and lead with intention.
The good news is you don’t need to overhaul everything overnight. Start with visibility. Build on collaboration. Invest in the tools and trust that make real-time security a daily reality, not a distant goal.
IoMT device security is mission-critical for healthcare in 2025, not because regulators dictate it, but because lives hang in the balance. The reality is stark: nearly every hospital in the U.S. has critical devices vulnerable to known exploits. Yet, with exposure-centric planning, smarter procurement, real-time monitoring, and collaborative leadership, the tide can turn.
Technology can heal. But only if we secure the tools we trust to do so.
FAQs
1. What exactly qualifies as an IoMT device in healthcare?
IoMT stands for Internet of Medical Things. It includes connected devices like infusion pumps, patient monitors, imaging equipment, smart beds, and wearable health monitors.
2. Why are these devices more vulnerable than standard IT systems?
Many run on outdated or proprietary systems that are difficult to patch. Furthermore, they lack the visibility and control mechanisms found in traditional IT infrastructures.
3. Can hospitals simply disconnect vulnerable devices from the internet?
Although a few can function without an internet connection, most depend on network access for updates, telemetry, and integration with EMRs. Consequently, it is not always practical or safe to take them offline.
4. What is the biggest obstacle to securing IoMT devices at present?
Obsolete infrastructure and lack of transparency. Due to the lack of accurate and real-time inventories of connected devices in most hospitals, it is challenging to determine which ones are genuinely vulnerable.
5. What is the single best first action for health systems just beginning on this path?
Assess device exposure. Prioritize devices with both identified vulnerabilities and internet connectivity; these are the biggest risk and easiest to target for remediation.Dive deeper into the future of healthcare.Keep reading on Health Technology Insights.To participate in our interviews, please write to our HealthTech Media Room at sudipto@intentamplify.com







